Function Hooking
Function hooking is a technique attackers use to modify/block/monitor original function calls and their intended purpose. There are a few ways to perform such an attack: Virtual Method Table hooking, Event hooks (ex: keyboard, implemented by Windows), Interception (by overwriting first bytes of the function with a jump) and Import Address Table (IAT) hooking (can be global or internal). This list in not comprehensive, but these methods are the most popular.
Let's start with the relatively easy method: interception. To make it visual and simple to follow, let's apply this method to a small program which sums two numbers together and multiplies the result by 2:
Once we compiled the program, we want to find magicSum function in the debugger:
Here we can see, that after original setup, mathematical calculation is being performed and then we return back to the where this function was called from.
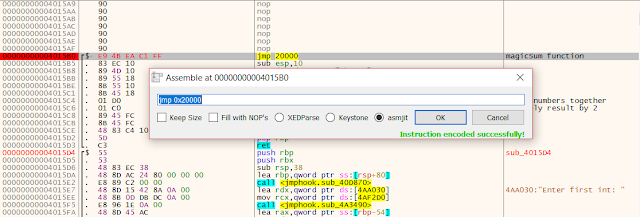
In order to intercept this function we will allocate a memory block in the program:
Next, we want to copy all instructions of the original function with our alterations:
As you can see, we removed a multiplication of the result by 2 and replaced it with nops (no operation), thus altering the result this function will produce.
Finally, we need to overwrite first few bytes of the original function to jump to allocated memory:
After executing the program, we can see that the magic sum is no longer magic:
Next, let's move on to the IAT hooking. This method is more complex, but at the same time more reliable. Here is a small diagram, explaining how it works:
The concept is similar to the interception, but instead of overwriting bytes of the function, we overwrite jump bytes in the Import Address Table, which point to the function.
For the sake of simplicity we will use a library called "MinHook". To make everything work, we need to compile MinHook with MinGW and place resulting DLL in the same folder as our project.
After we compile and execute our project we will see that first message box is displayed as it was intended (exactly how it was specified in the code), but because we enable the hook before calling the second identical message box, we display what parameters will be passed to the function, modify one of the parameters and pause the program for the user to see. Such hook can be easily integrated into a DLL and injected into a process. If you are interested in how it can be done and ways to detect it - check out this post.
Well, hooks can be used for a wide variety of tasks, such as: game exploitation, cheat development, license bypass, etc. It is important to protect your software to prevent hackers from interfering with user experience and your product being cracked.
How can one protect from such an attack?
If an attacker injected a DLL to hook functions, then we can simply check for loaded modules like mentioned in this post. If attacker used an interception method, then we can simply obtain hash of the function (opcodes) we want to check and compare it to the value stored somewhere in advance. Another option is to implement active scanning for the allocated memory blocks and validate which blocks are not supposed to be there (allocated by an attacker).
In case an attacker uses more complex hooking methods (such as IAT hooks), having a driver restricting outside programs read and write access to the memory of our process will ensure safety of our software. Other, simpler, solution would be to monitor stack trace logs or run important code in an emulated environment, where we can control, closely monitor, and detect changes to our program in runtime.
References and useful links:
https://en.wikipedia.org/wiki/Hooking
https://github.com/TsudaKageyu/minhook
http://jbremer.org/x86-api-hooking-demystified/
https://ocw.cs.pub.ro/courses/so/laboratoare/resurse/injections
https://www.unknowncheats.me/forum/c-and-c-/72416-simplest-function-hooking-ida-detours.html
Let's start with the relatively easy method: interception. To make it visual and simple to follow, let's apply this method to a small program which sums two numbers together and multiplies the result by 2:
Once we compiled the program, we want to find magicSum function in the debugger:
Here we can see, that after original setup, mathematical calculation is being performed and then we return back to the where this function was called from.
In order to intercept this function we will allocate a memory block in the program:
Next, we want to copy all instructions of the original function with our alterations:
As you can see, we removed a multiplication of the result by 2 and replaced it with nops (no operation), thus altering the result this function will produce.
Finally, we need to overwrite first few bytes of the original function to jump to allocated memory:
After executing the program, we can see that the magic sum is no longer magic:
Next, let's move on to the IAT hooking. This method is more complex, but at the same time more reliable. Here is a small diagram, explaining how it works:
The concept is similar to the interception, but instead of overwriting bytes of the function, we overwrite jump bytes in the Import Address Table, which point to the function.
For the sake of simplicity we will use a library called "MinHook". To make everything work, we need to compile MinHook with MinGW and place resulting DLL in the same folder as our project.
After we compile and execute our project we will see that first message box is displayed as it was intended (exactly how it was specified in the code), but because we enable the hook before calling the second identical message box, we display what parameters will be passed to the function, modify one of the parameters and pause the program for the user to see. Such hook can be easily integrated into a DLL and injected into a process. If you are interested in how it can be done and ways to detect it - check out this post.
Well, hooks can be used for a wide variety of tasks, such as: game exploitation, cheat development, license bypass, etc. It is important to protect your software to prevent hackers from interfering with user experience and your product being cracked.
How can one protect from such an attack?
If an attacker injected a DLL to hook functions, then we can simply check for loaded modules like mentioned in this post. If attacker used an interception method, then we can simply obtain hash of the function (opcodes) we want to check and compare it to the value stored somewhere in advance. Another option is to implement active scanning for the allocated memory blocks and validate which blocks are not supposed to be there (allocated by an attacker).
In case an attacker uses more complex hooking methods (such as IAT hooks), having a driver restricting outside programs read and write access to the memory of our process will ensure safety of our software. Other, simpler, solution would be to monitor stack trace logs or run important code in an emulated environment, where we can control, closely monitor, and detect changes to our program in runtime.
References and useful links:
https://en.wikipedia.org/wiki/Hooking
https://github.com/TsudaKageyu/minhook
http://jbremer.org/x86-api-hooking-demystified/
https://ocw.cs.pub.ro/courses/so/laboratoare/resurse/injections
https://www.unknowncheats.me/forum/c-and-c-/72416-simplest-function-hooking-ida-detours.html








Comments
Post a Comment